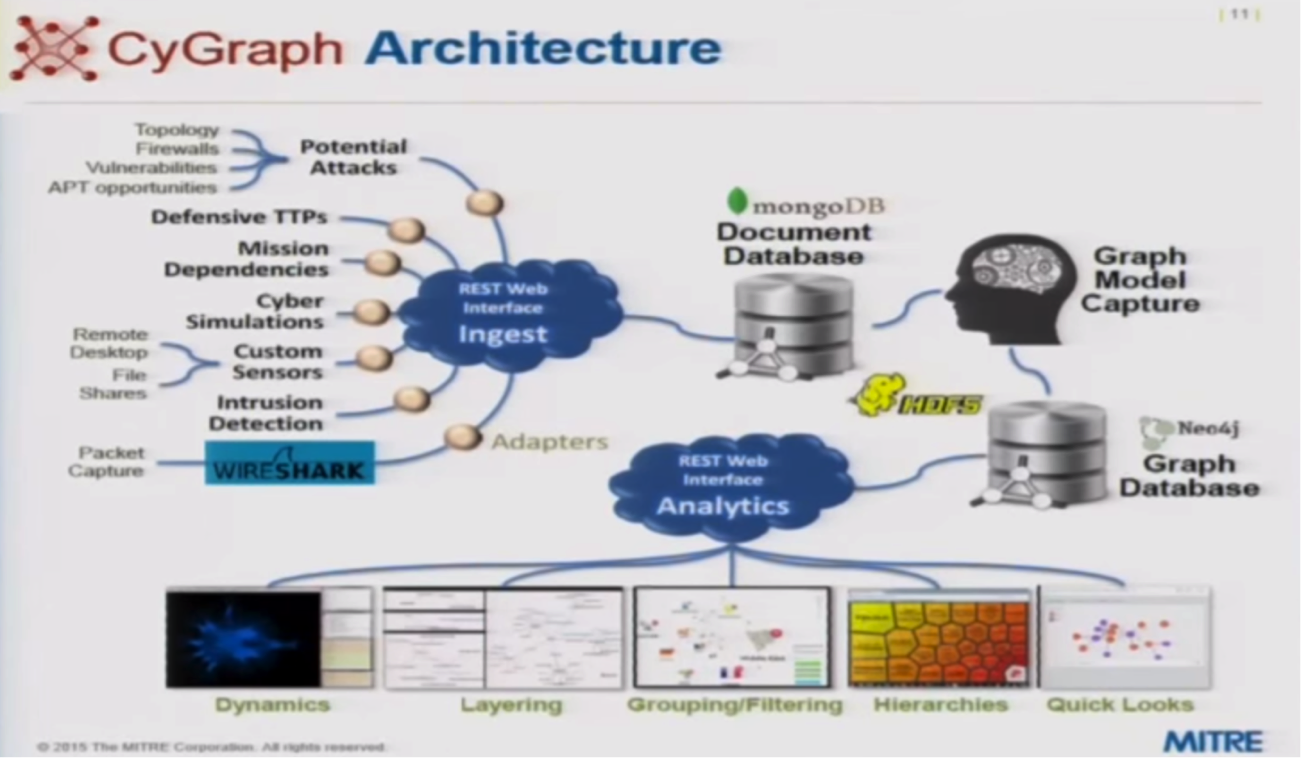
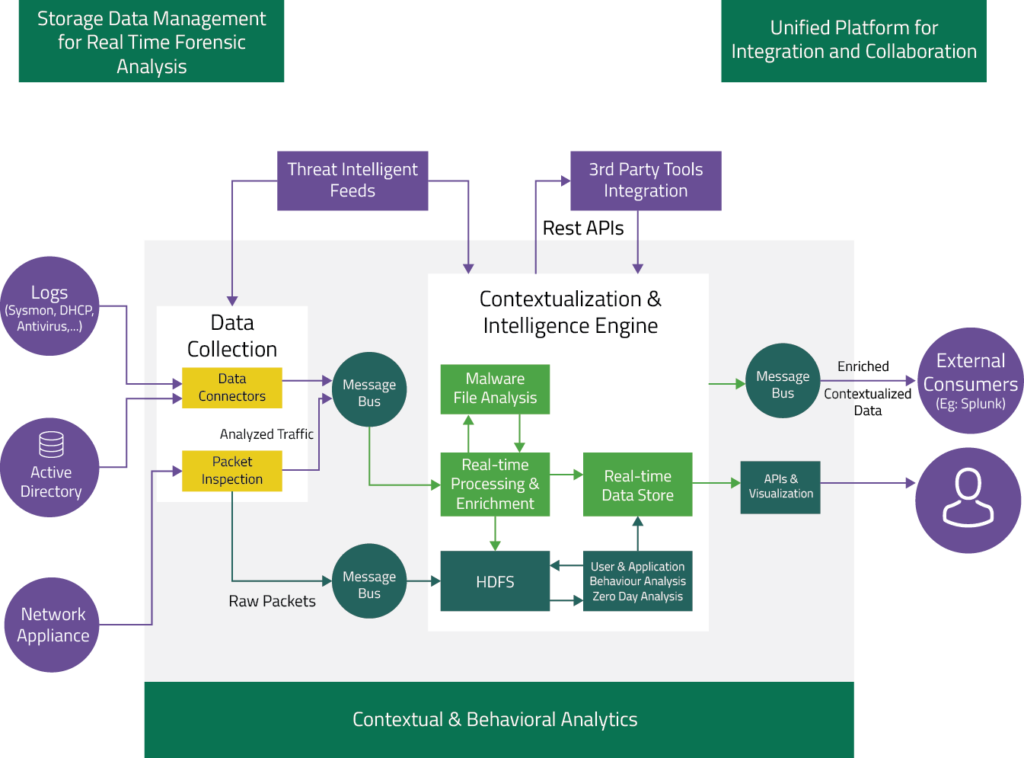
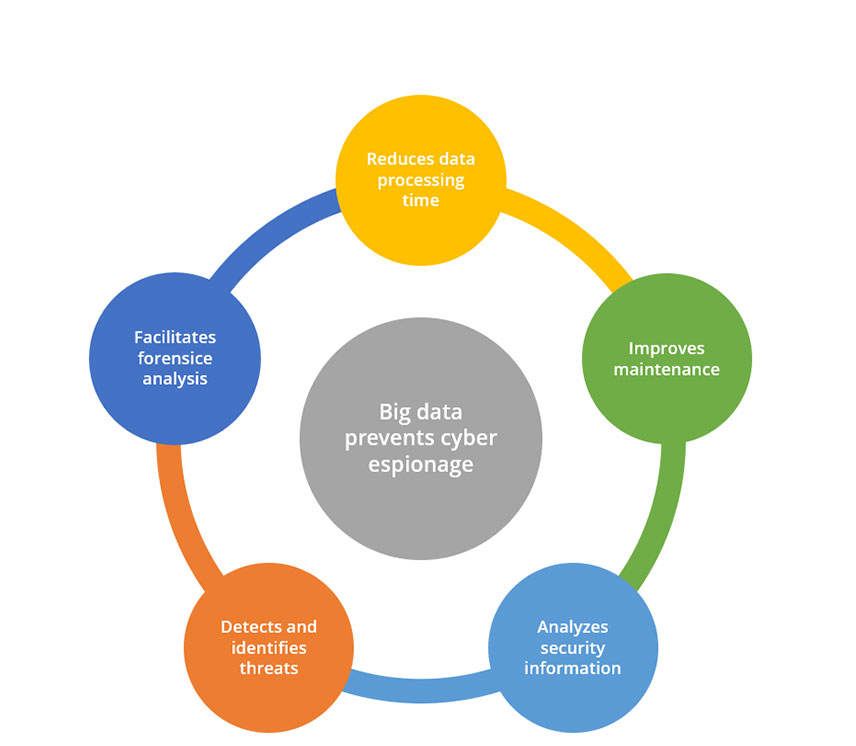
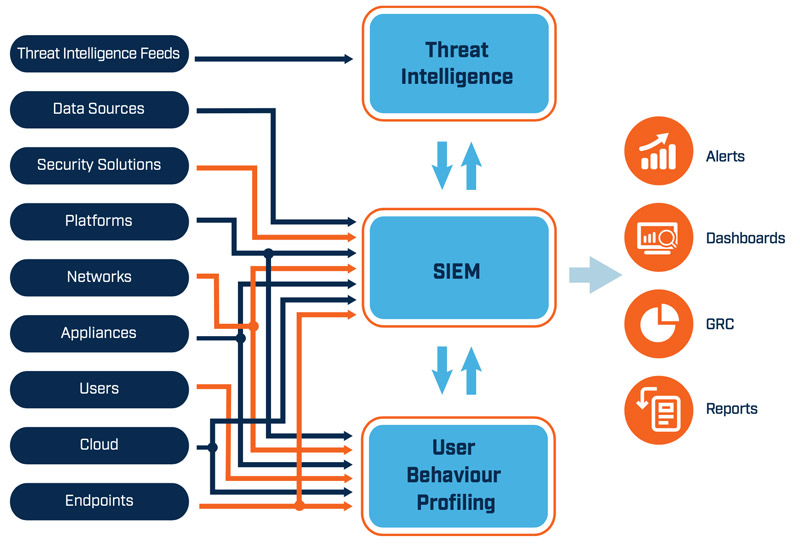
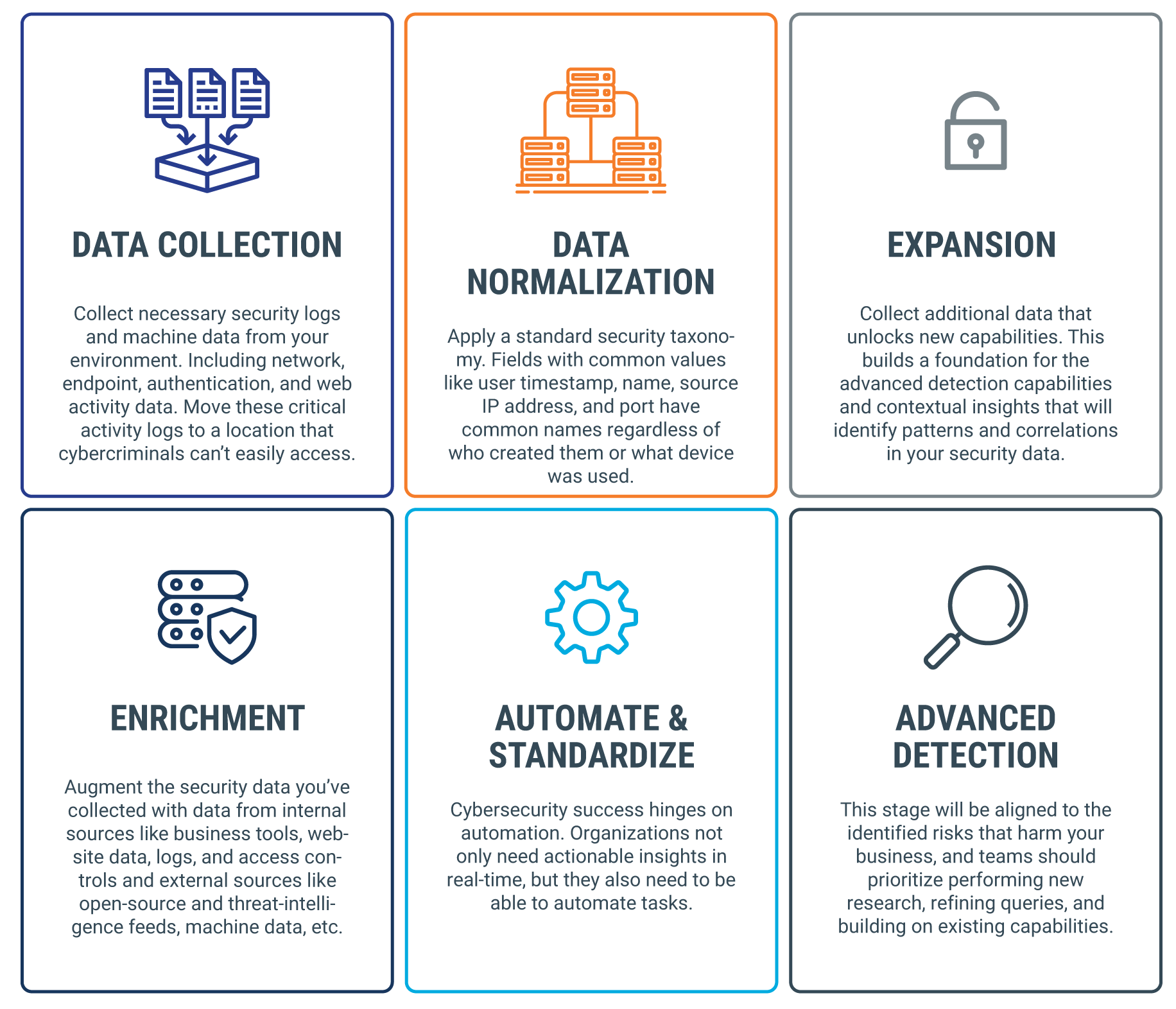
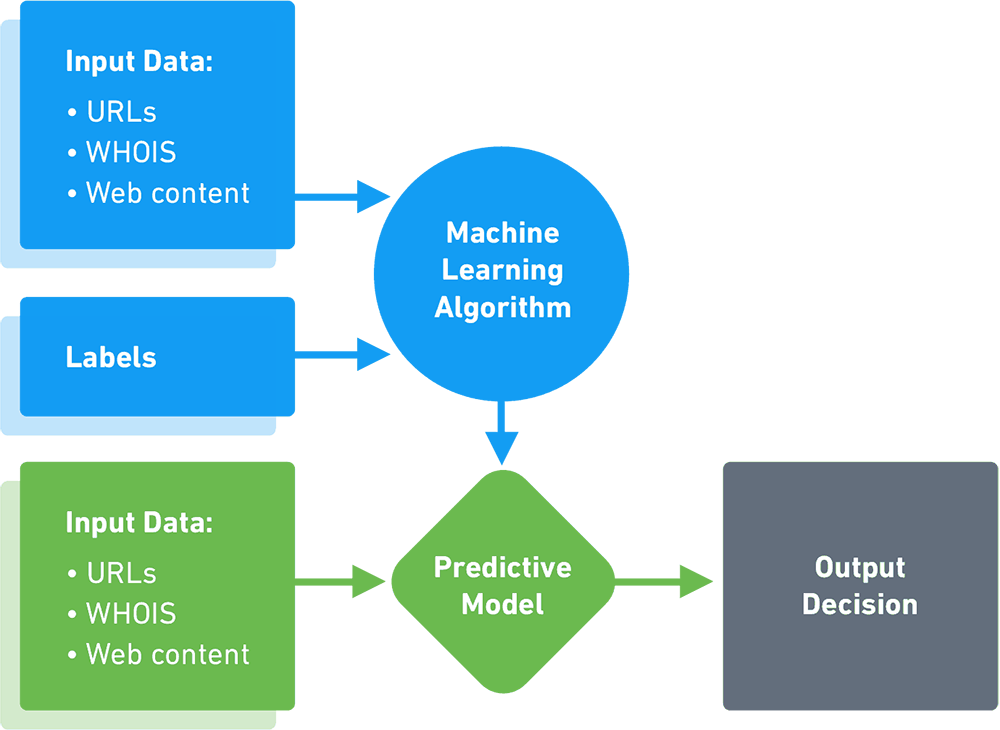
How Big Data and Analytics Can Help Businesses Improve Cybersecurity | Customer-centric product development and innovation

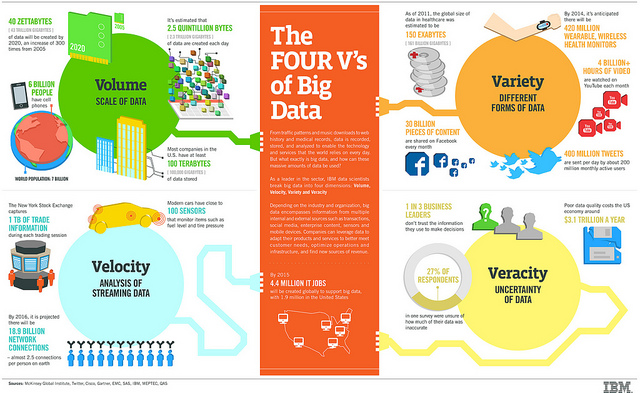
The Challenges and Opportunities of Big Data in Cybersecurity | Data Center Knowledge | News and analysis for the data center industry